
The automotive industry is transitioning to Software-Defined Vehicles (SDVs) to provide more flexibility in vehicle software. SDVs differ from vehicles manufactured in the past in many ways, not the least of which is that they require mixed-criticality systems and the option to easily shift software applications, functions, and features between hardware resources seamlessly.
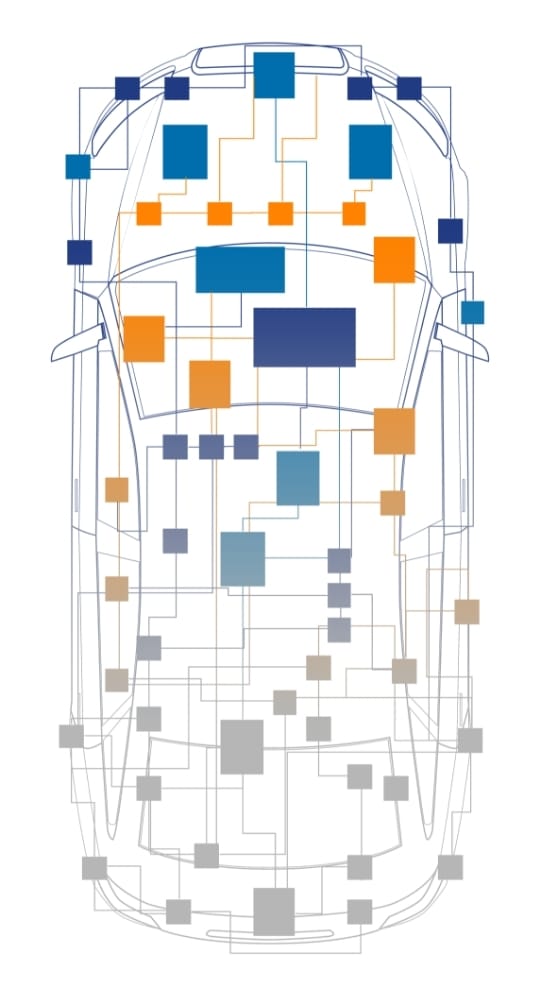
Today’s automotive software (SW) development creates software components (SWCs) embedded across more than 100 electronic control units (ECUs). The integration of all these SWCs generates a monolithic block of SW that is difficult and time consuming to maintain. Any SWC change or addition requires re-testing of the entire package leading to extremely lengthy development cycles before deployment. While software abstraction is the first step to solving this challenge, SDVs require full hardware abstraction as well to decouple the platform and application. This enables a commonality between different HW platforms and the reuse of corresponding software components throughout the vehicle.
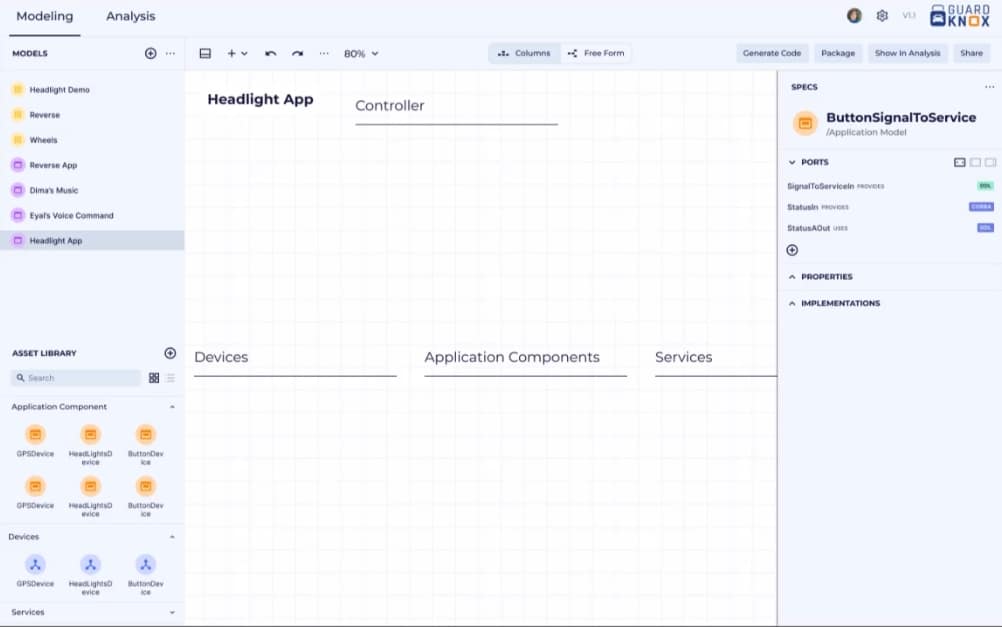
It’s never been easier or faster to create, modify, update, or change automotive software and then seamlessly deploy on target thanks to our dedicated developer tool suite. The tool suite provides model-based SW component development tools that cover the entire development lifecycle from initial development with automatic code generation, through debugging, testing, deployment and post-deployment analysis for streamlined integration.
The tool suite uses a modern and secure approach to automotive software management that enables drastically faster time to market for new services and applications.
Experience the leanest automotive middleware solution purpose-built for embedded systems. The SOA core framework middleware abstracts all components in a vehicle (+ cloud), enabling the complete decoupling of HMI, applications (or SW services) and OS from the lower levels such as Hypervisor, Secure Separation Kernel and Hardware.
It’s built on an open-source architecture that’s automotive domain-agnostic and optimized for embedded systems and addresses heterogeneous environments (HEMs).
Features and functions are implemented as services that communicate via well-defined message-based interfaces. This provides the needed hardware abstraction on both the ECU and vehicle level as well as enables standard API’s, opening up the possibility for 3rd Party development.

GuardKnox’s SOA Framework consists of several core components providing the infrastructure and environment for automated and dynamic software life cycle management. Based on the Framework, solutions can be easily created for a single software-defined ECU all the way up to a full software-defined E/E architecture extending into the cloud.
The design is open and extensible and features cross-platform support. ‘Platform’ is defined as consisting of a CPU architecture, hypervisor and partition OS. Several MPUs, MCUs and partition OSs are supported. GuardKnox’s SOA framework integrates with AUTOSAR Adaptive to reuse existing concepts and implementations, allowing significant reduction in development time and costs.
The framework supports multiple communication interfaces concurrently, and it can accommodate middleware implementations based on CORBA, DDS, SOME/IP, and more.
The SW lifecycle within an ECU is managed automatically: SWCs are automatically deployed, initialized, started, stopped, torn down and removed. A deployment decision for a SWC can be automatic, based on a resource manifest allowing deployment to occur across heterogenous E/E architectures.
GuardKnox’s toolchain allows system architects to utilize multiple components from pre-existing frameworks and automatically create a hypervisor configuration and partition images using a graphical interface resulting in faster time to market and lower development costs.
GuardKnox’s Secure SOA Framework includes the following deliverables based on customer needs:
Below is an example of a generic framework using GuardKnox’s SOA approach deployed on a domain with 2 ECUs. (1 central computer & 1 gateway controller, 2 gateways controller, 1 gateway controller & 1 ECU, etc.)
On top of the hardware there is the Secure Separation Kernel (SSK). A separation kernel is a SW layer which creates an environment that is indistinguishable from that provided by a physically distributed system. The secure separation kernel adds sophisticated security functions to the separation functions.
On top of the SSK is the hypervisor that creates a Virtual Machine (VM) environment. For this purpose it emulates a HW platform on which multiple guest partitions with their respective Operating Systems (OSs) can run. This means that for a Guest OS it is indistinguishable whether it runs on top of a hypervisor or directly on top of a processor HW.
On top of each Guest OS and the common functions SOA Node Manager and SOA Port there are one or several applications that have been developed for this particular OS. The applications, common functions and their OS form a node. One particular node is the Central Management node which manages the entire GuardKnox SOA Framework.
AUTOSAR Adaptive has increasingly been adopted for SW development in the automotive industry. A number of applications have been implemented already and are available to be (re-)used. GuardKnox’s SOA Framework, however, is more powerful and provides a much more comprehensive approach to the entire SW lifecycle. Instead of having to re-implement the existing AUTOSAR Adaptive applications, they are directly supported within GuardKnox’s SOA Framework. They run on dedicated nodes, with their own specific OS. The SOA Node Manager ensures that AUTOSAR Adaptive messages are properly routed within the system.
A SWC can be manually and automatically relocated, by the SOA Framework, into a compatible node or even another compute platform whether on-vehicle or in the cloud. When the source was compiled using a supported compiler for a compatible OS, it can be seamlessly shifted to a different partition. Otherwise, a POSIX-compliant SWC can be built and activated on top of any OS and hypervisor which is POSIX compliant.
GuardKnox’s SOA Framework is even powerful enough to shift node containing an OS and applications between ECUs and even between compatible hypervisors.
Access to the virtualized communication infrastructure is seamlessly mediated through the SOA Framework, allowing for virtualized Remote Procedure Call (RPC) and data exchange.